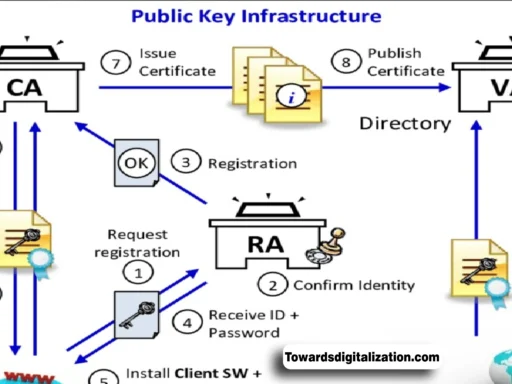
Introduction
In the digital age, mobile phones play a vital part in helping to provide continuous, and connectivity in enterprises. However, their widespread use could also create security issues and problems with management. An organized mobile device policy is necessary for tackling these issues and fully utilizing the power of mobile technology.
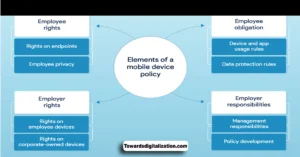
1. Purpose of the Mobile Device Policy:
The Mobile Device Policy provides complete guidelines for security. In addition to promoting the efficient use of mobile devices, whether personally or company-owned, this policy also aims to protect sensitive company information. Furthermore, it seeks to minimize the risk of security breaches while ensuring compliance with relevant laws and regulations. This policy provides guidelines on how to use smartphones in the workplace. It also offers recommendations for dealing with security concerns.
A properly thought-out mobile Device Policy will ensure clarity regarding employees’ roles and responsibilities. It outlines clear expectations for employees and assists businesses in protecting their investments. Mobile devices are now vital instruments in everyday operations. They allow employees to be productive when working remotely and on the go. If not controlled correctly, they could be an open door to cyberattacks.
2. Scope of the Mobile Device Policy:
The mobile device policy applies to any employees, contractors, or other vendors who use third-party devices to access the company system, network, and data. It also covers laptops, wearables, and different computing devices on the move. Additionally, the policy applies regardless of the device’s owner, as well as the device’s employees and corporate use in the work environment.
This policy also applies to service providers who are outside parties who can gain access to organizational information through phones. This policy’s conformity is essential to ensure that the organization complies with these guidelines, which could result in consequences, like the removal of access privileges and penalties for violating the legal requirements in the instance of a data breach.
3. Acceptable Use in the Mobile Device Policy:
The safe and proper utilization of mobile devices will ensure that users use technology safely, responsibly, and efficiently.These guidelines provide clear instructions on the acceptable usage of mobile devices. Firstly, mobile devices must be used exclusively for official business purposes. Additionally, access to the company’s network and data must be secured through approved applications and encrypted connections.
While the company generally restricts personal use of company-owned devices, employees must strictly follow company policies for any permitted use. Additionally, they must not install unauthorized software or modify device settings. They are also prohibited from accessing, downloading, or storing inappropriate or offensive content using company resources.
Employees should stay vigilant when using company systems in public places and ensure unauthorized individuals cannot view sensitive information. Furthermore, they should use Virtual Private Networks (VPNs) when accessing company systems remotely.
4. Security Requirements:
Security is an essential aspect of managing the security of mobile phones. The following security guidelines are mandatory for all smartphones.Devices must be secured using strong passwords, pins, and biometric verification.Configuring the device to shut down automatically after an inactivity period is essential.Updates to software and security are frequently up-to-date. Updates must be implemented quickly.
If this isn’t possible, they should use VPN options to create safe connections.
5. Bring Your Own Device (BYOD) Policy:
The Bring Your Device (BYOD) Policy allows employees to use their devices to work according to the business’s security regulations.The IT department must approve employees before they use personal devices. Employees must ensure their devices comply with the minimal security standards set by the business if they use them for personal purposes. All employees must download security software for their devices. The company requires that its data be accessible and saved only in certified software. Employees must regularly check their personal devices for updates and ensure they are free of malware.
The business reserves the right to demand the remote deletion of files stored on employee-owned devices in the instance of theft, loss, or the destruction of the termination of employment.
6. Data Privacy and Protection in the Mobile Device Policy:
Data security is a fundamental necessity for companies. Mobile device users must not save sensitive company information on other storage devices. They must ensure that sensitive files are safely deleted. Users should delete documents when they are no longer required. They must follow the company’s guidelines regarding data retention. Users should avoid sharing their details via insecure messages or email services.
Employees must be aware of and in conformity with lawful privacy laws that apply in their areas of responsibility. Information transmitted and received by mobile devices must be secured and securely stored.
7. Monitoring and Compliance:
To ensure compliance with the Mobile Device Policy, the business may monitor the following: the use of devices connected to enterprise networks, access logs to identify suspicious activities, and applications installed on company-owned devices.
Any violation of the Mobile Device Policy may result in the enactment of discipline, which could consist of either a permanent or temporary removal of access to the device or removal or termination of work.
8. Employee Responsibilities Under the Mobile Device Policy:
Every employee bears the obligation to ensure your mobile device’s security and adhere to this rule. The most crucial responsibilities of an employe. Mobile devices must be handled with caution in the workplace.Ensure the devices are secure and never kept in unsafe areas or public spaces.Notifying of any security breaches or stolen devices and to the IT team as soon as possible.Use the instructions from the IT department to maintain software and updates.Beware of any modifications not permitted.
Employees also have to attend regular training sessions to stay informed about the security features of mobile devices and company policies.
9. Incident Response Plan:
In the event of a security breach or any incident involving mobile devices, the following steps must be followed: First, immediately notify the IT department of the issue. Next, isolate the affected device from the corporate network to prevent further risks. Then, assess the significance and impact of the incident. Afterward, follow the organization’s established incident response procedure. Finally, document the incident thoroughly for future analysis and improvement.
10. Policy Review:
The Mobile Device Policy will be periodically reviewed or updated as needed to ensure that it is current and pertinent to the most recent threats and advancements in technology.
11. Reference :
- Bring Your Own Device Policy
- Access control Policy
- Media disposal policy
- Acceptable use of information assets policy
- HR IT Policy